What Does Our Free Phishing and Training Tool Do?
What is CYBERDISE Freemium Edition?
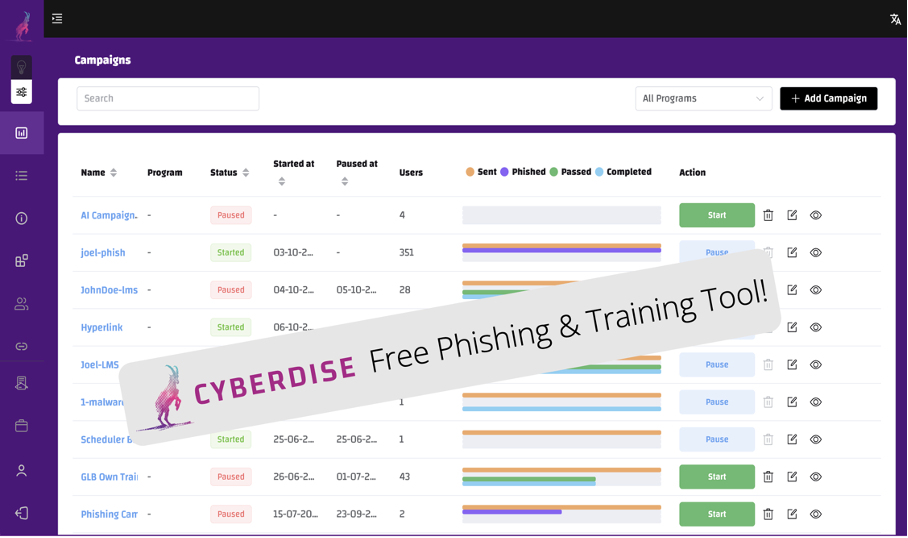
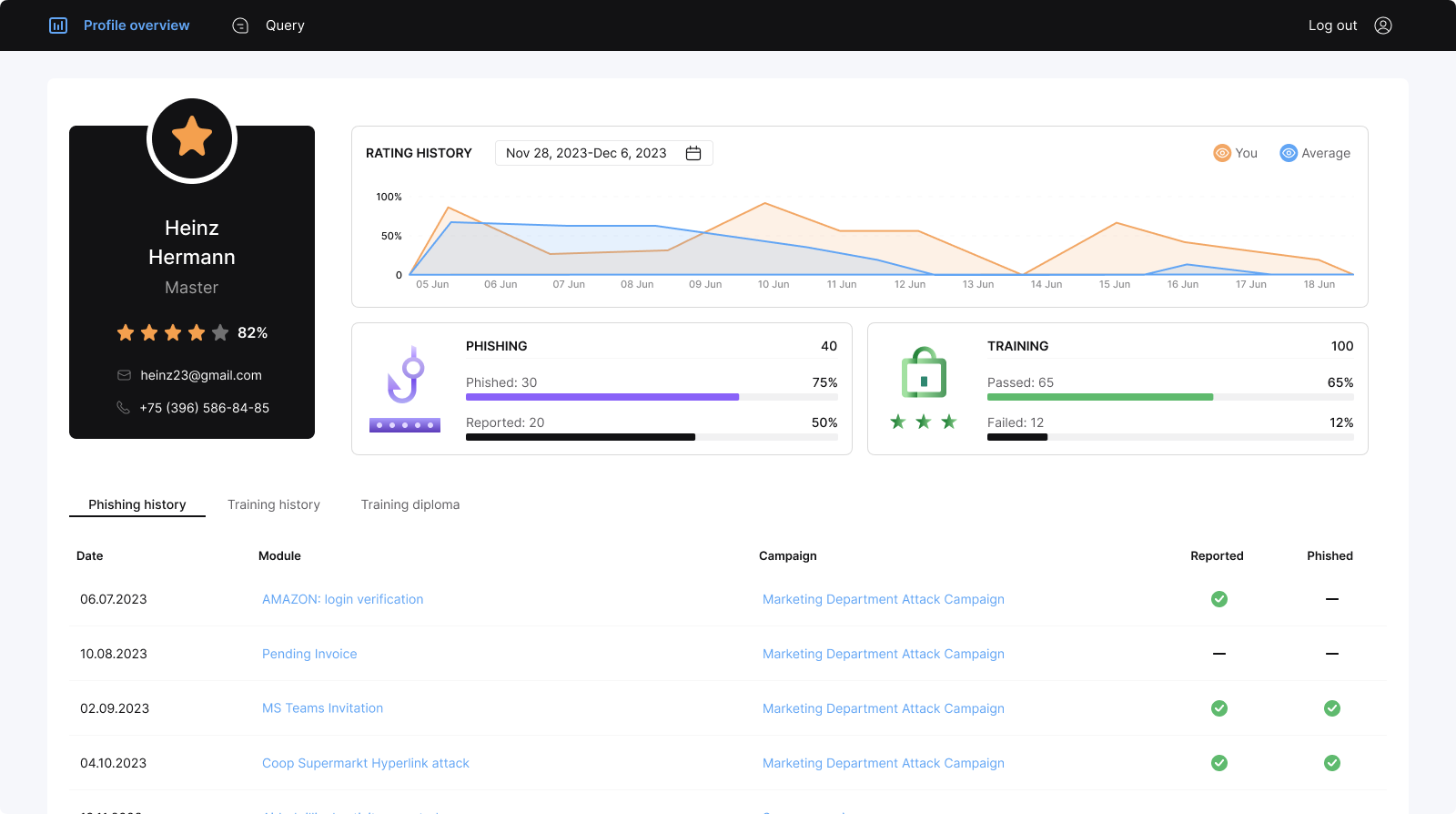
It is a free phishing tool and learning environment where users can complete cybersecurity courses. Technically speaking, it is an attack simulator and a lean LMS including a content editor and user management.
What does the solution include?
The phishing simulator, learning management functionalities, two dozen attack templates, a dozen e-learning modules on information security, a content editor for customizing templates, and recipient management.





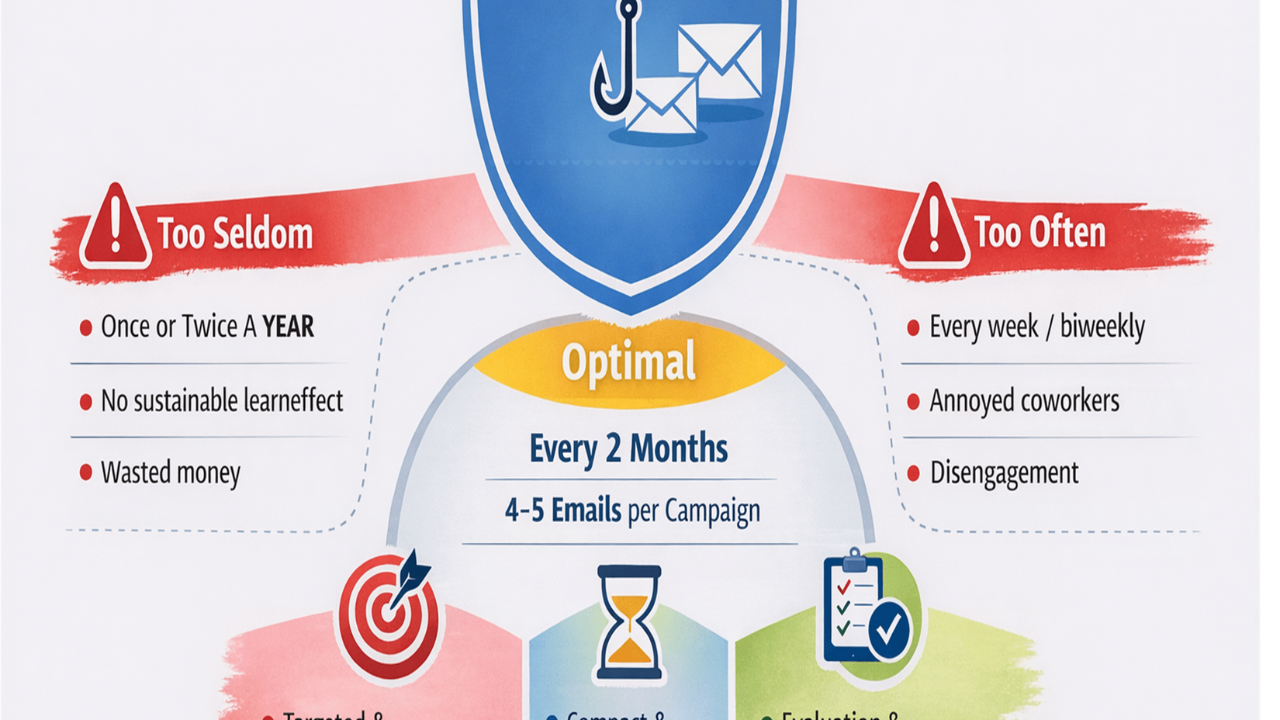







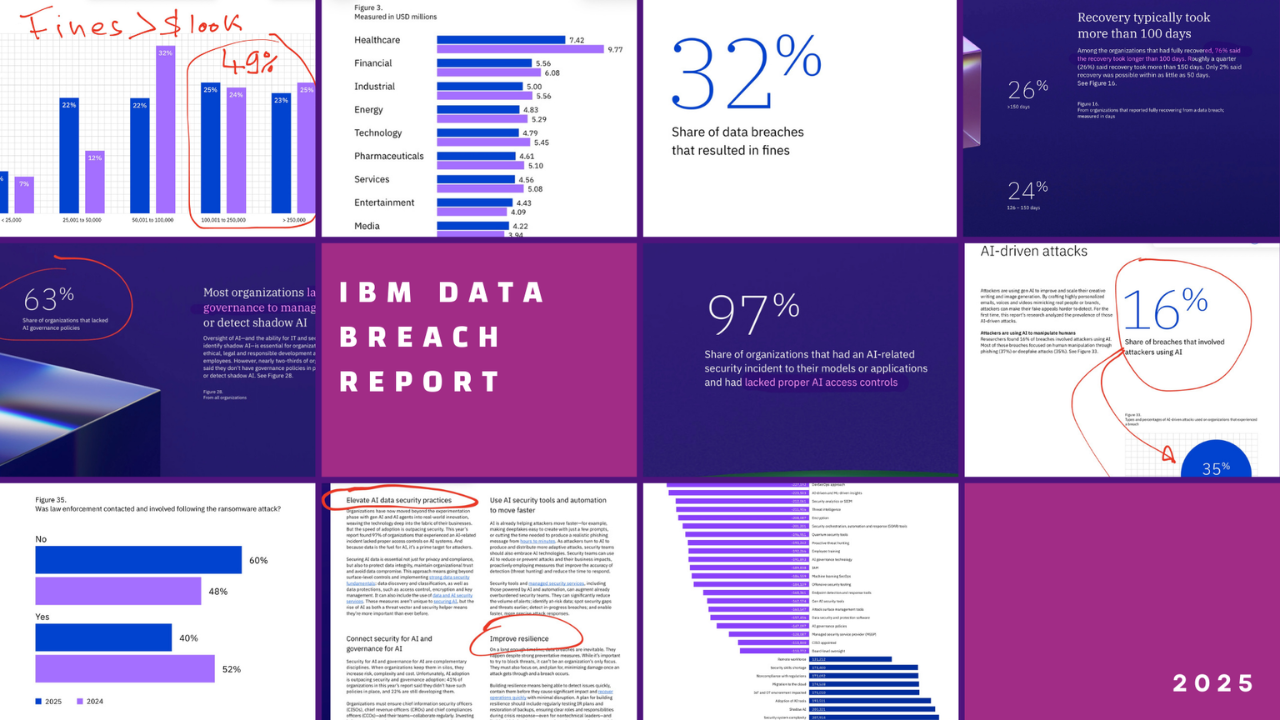
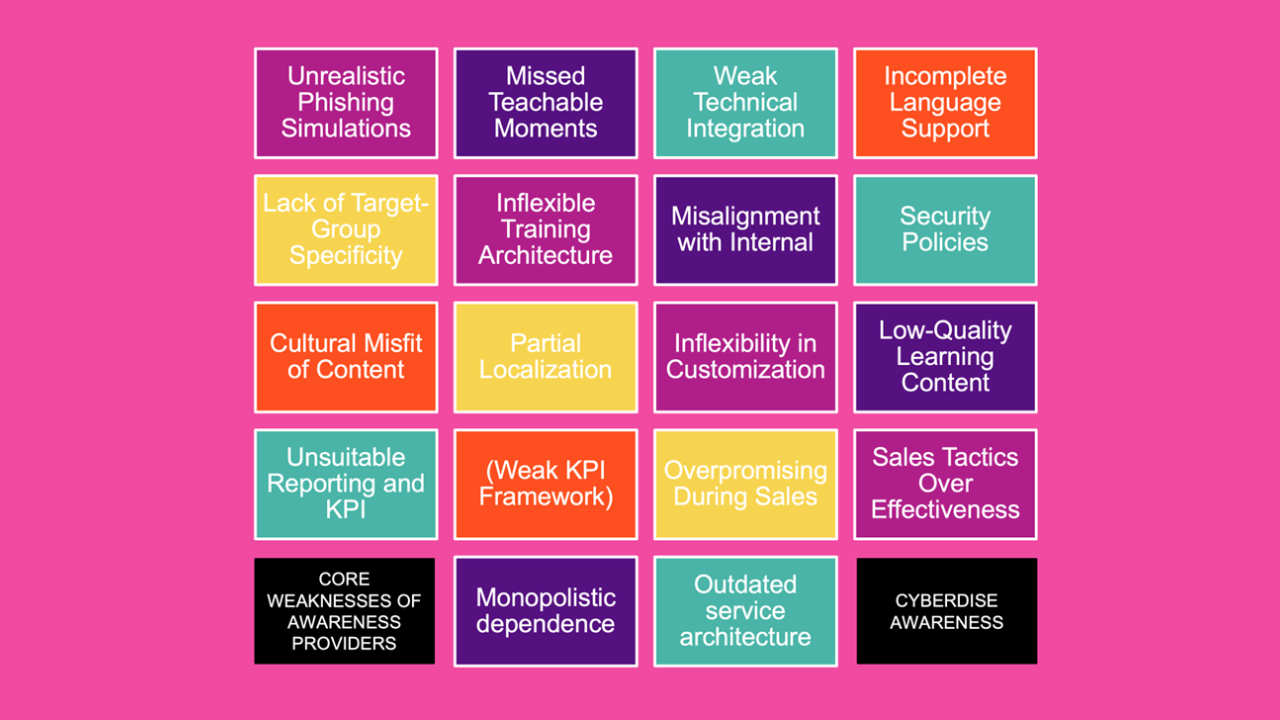







![Cybersecurity News: From AI Scams to Quishing [2024]](https://cyberdise-awareness.com/wp-content/uploads/2024/11/фпафап-e1730818260120.png)