What the 2025 IBM Data Breach Report Really Says?
The IBM Cost of a Data Breach Report has been published every year for two decades.
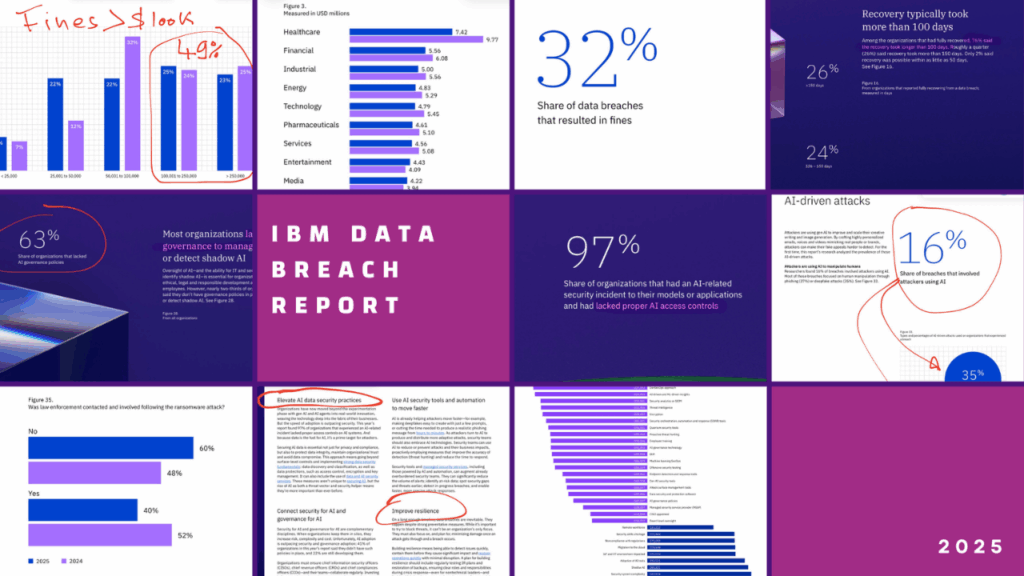
It’s often read for the numbers: the global average breach cost (now $4.4M), the top industries, or the fines (which in the U.S. push average costs to $10M).
But look a little deeper and with your own expert-view, and this year’s report says something more fundamental about cybersecurity awareness.
AI is already inside the breach.
One in six breaches in 2025 involved AI.
And when AI was used, attackers reached for tools we all “know very well”:
37% were phishing emails
35% used deepfakes and impersonation
Phishing remains the dominant entry point. The difference is scale and realism. AI doesn’t replace old attack vectors – it makes them much stronger.
Governance is the missing piece.
63% of organizations hit by an AI-related breach had no AI governance in place.
97% lacked access controls for AI tools.
This explains why “shadow AI” – employees experimenting with tools outside IT’s oversight – shows up so frequently in breach narratives. We’ve seen the same pattern before: adoption moves faster than security.
To those who have been waiting for the “Would You Rather” Poll Results from Previous Newsletter Issue: 49% would rather read every internal security policy and 51% would rather build instincts to stop risky clicks. Almost perfectly balanced nose to nose. We were very surprised! 😉
Recovery is harder than many admit
- Two-thirds of organizations say they never fully recover from a data breach.
- And 76% say recovery takes longer than 100 days.
These numbers put the focus on resilience — not just prevention. If most companies can’t bounce back quickly, the conversation has to shift toward how people react under attack.
So what does this mean for awareness?
The report’s numbers confirm what awareness professionals have long observed:
Attack vectors stay constant (phishing, compromised credentials, insider threats).
The environment around them evolves (AI, automation, fines, supply chains).
Human error is still the constant.
What changes is the context in which humans make mistakes.
That’s why traditional awareness (policies, lectures, slide decks) rarely works under real pressure. People know the rules — but fatigue, urgency, or a very convincing AI-crafted phish are enough to override that knowledge.
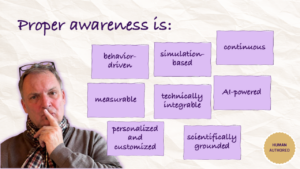
The answer is not more policies. It’s practice.
Realistic simulations. Adaptive coaching. Building instincts instead of relying on theory.
“The IBM report reminds me: awareness is not about knowing what phishing is. It’s about building the muscle memory to resist it – even when the phish looks perfect.”
– Palo Stacho
Results From Joint Study With Lucerne University: AI-Enabled Spearphishing

In collaboration with Lucerne University, CYBERDISE conducted a controlled study to examine how employees respond to AI-enabled spearphishing attacks. Unlike traditional phishing, these attacks are personalized, adaptive, and more difficult to detect.
The research reveals a clear finding: Participants trained with CYBERDISE demonstrated a 60% increase in vigilance when facing AI/OSINT-generated spearphishing attempts. In this webinar, we will present the study design, key results, and implications for organizations that want to stay ahead of evolving threats.
You’ll learn:
– How AI is reshaping the landscape of spearphishing.
– The methodology and findings from our joint study with Lucerne University.
– Why human vigilance remains a major vulnerability in cybersecurity.
– Practical advice to strengthen awareness programs based on scientific evidence.
[1] https://www.ibm.com/reports/data-breach
We’re excited to share more cybersecurity insights, news, and updates with you in the upcoming editions of this newsletter. However, if you don’t find this helpful, we’re sorry to see you go. Please click the unsubscribe button below.