What CUSTOMERS DO WRONG when starting Cybersecurity Awareness Programs
Published Date:
- December 1, 2025
Common possible missteps on customer-side in implementing Security Awareness projects
It’s like any other project: you think it’s too easy, you don’t listen or listen to the wrong experts, you think you’ll master it, or you think you can do it alone, you don’t talk to each other enough and the goals and requirements are not as clear as they should be. If you then start with an inappropriate mindset and management fails to recognize the purpose, value and benefits of awareness, then the project can get off to a very bumpy start.
This is also sometimes the case with the introduction of cybersecurity awareness programs.
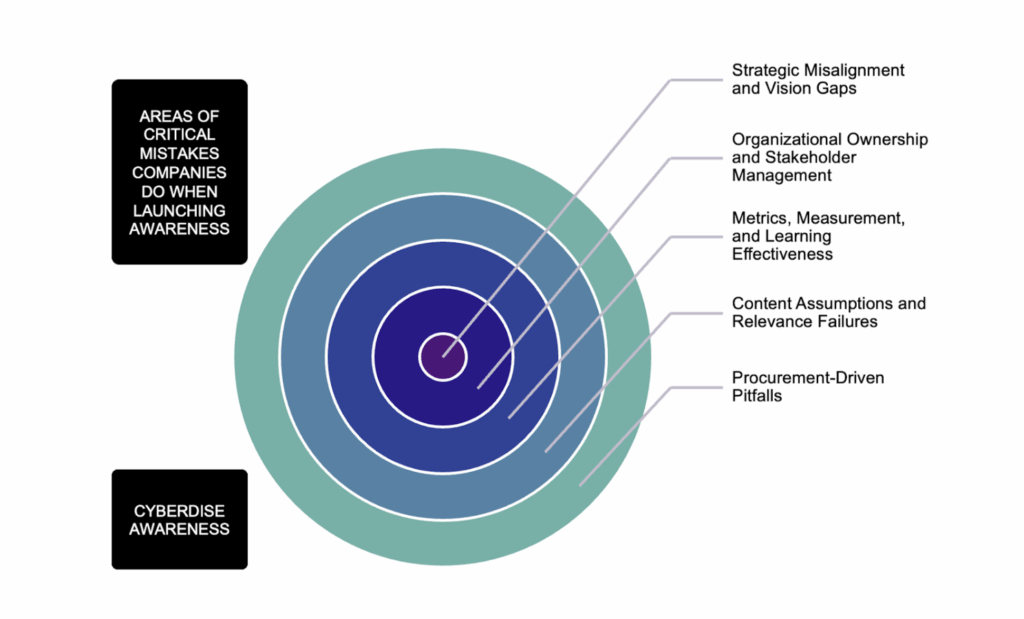
To take a look at what can go wrong, we have examined the mistakes and false expectations that were documented in a USENIX study [1]. We then compared the results with our own experience and structured and completed the list.
The outcome is a summary of shortcomings, blind spots, and false assumptions made by organizations/customers when procuring or starting to operate phishing simulation and awareness programs. That’s what we find out:
- Assuming Awareness Is Plug-and-Play
- Underestimating Stakeholder Involvement
- Lack of Internal Project Ownership and Clear Project Goals
- Overvaluing Click Rates and Phishing KPIs
- Assuming Content Quality Without Validation
- Neglecting Master Data Quality
- Treating Security as “Someone Else’s Job” or “The Suppliers Job”
- Choosing Vendors Based on Price Bundling
- Overemphasis on Training, Not Testing
- Fear of Frightening Employees with Cyber Awareness
- No Metrics for Learning Outcomes
- Lack of Planning for Time and Resources
- Assuming One-Size-Fits-All for Global Teams
- Over-Reliance on Security Teams
- Ignoring Integration Challenges
- Procurement Effort Exceeds Project Execution Efforts
- Focusing on Content Instead of Service Capability
- Treating Awareness as a Compliance Checkbox
Common Pitfalls in Cybersecurity Awareness Projects
- Assuming Awareness Is Plug-and-Play:
For bigger organizations it’s not easy nor simple. Believing that SAC/PSC is a low-effort, plug-and-play solution is a fundamental mistake. Many organizations assume the rollout is quick and easy, when in reality it requires over 14 months and significant cross-functional effort. - Underestimating Stakeholder Involvement:
More departments are usually involved than expected. In the studied organizations, up to 17 departments participate. It’s crucial to engage all stakeholders early – before the project starts – to prevent delays, frustration, and additional costs. - Lack of Internal Project Ownership and clear Project Goals:
Tasks like content review, testing, and integration are not clearly assigned, resulting in missed deadlines and poor learning content coverage. Project goals are not clearly defined so project success is often unclearly measured. - Overvaluing Click Rates and Phishing KPIs:
Organizations often rely too heavily on raw click and report rates as indicators of success, without evaluating actual behavioral change or content quality. There is no structured survey of the level of awareness before and after the project launch. - Assuming Content Quality Without Validation:
Decision-makers often assume the awareness content meets company needs without reviewing its alignment with policies, tone, cultural fit or accuracy. - Neglecting Master Data Quality:
Do you want to train and phish meeting rooms? Many rollout issues stem from outdated or inconsistent employee data, such as incorrect email addresses or department mismatches. - Treating Security as “Someone Else’s Job” or “The Suppliers Job”:
Security and awareness responsibilities are expected to be added on top of daily tasks, leading to stakeholder overload or disengagement. In the worst case there’s an expectation that the vendor will take care of the doing. In the domain of cybersecurity awareness & training there is a widespread misconception that you have nothing more to do with awareness if you hand over the job to so-called full service awareness providers. - Choosing Vendors Based on Price Bundling:
Procurement prioritizes bundled Security Awareness Campaign deals for price benefits, even when content quality, culture fit, content adoption capabilities or technical capabilities are lacking. Neglecting to examine the range, quality and pricing of services for more individual services also happens frequently. - Overemphasis on Training, Not Testing:
Organizations assume users will learn from eLearning courses and ‘teachable moments’ during training, but many users lack awareness for awareness. Therefore they ignore or resent training nudges. Simulated attacks and assessments are underutilized. - Fear of Frightening Employees with Cyber Awareness:
Some fear that unannounced simulations will scare employees. However, experience shows this fear is exaggerated and not representative of overall workforce reaction. You can also announce the phishing tests in advance without any problems. The impact on the click rate will hardly be noticeable. - No Metrics for Learning Outcomes:
There is often no pre- or post-assessment to measure learning. Only operational metrics like clicks and threat reports are used, offering no insight into actual knowledge gain. - Lack of Planning for Time and Resources:
Time and effort are not formally budgeted or underestimated. Period. Annotation: The cheapest incident is the one which never happens, right? But how do you want to quantify such things? - Assuming One-Size-Fits-All for Global Teams:
Language barriers, privacy laws, and cultural differences are common but rarely anticipated or addressed in advance. The problem is the mindset lying beneath, that standard modules fit the custom needs of the company. - Over-Reliance on Security Teams:
Business units expect InfoSec to handle everything, even though InfoSec often lacks the capacity or the content knowledge required for Cybersecurity Awareness Program evaluation and operation. Often there’s also a skill mismatch: Security Teams are mainly protectors, Security Awareness Programs need more playful ‘preventers’ and educators. - Ignoring Integration Challenges:
Organizations assume the phishing simulation campaigns integrate seamlessly with internal systems (e.g., mail servers, firewalls, APIs), but in practice, this is rarely the case. Proper whitelisting is fundamentally important for the success of awareness campaigns and is always the responsibility of the company. - Procurement Effort Exceeds Project Execution:
More effort goes into supplier selection than the awareness project itself. There is a false belief that selecting the right solution ensures success. Moreover, procurement complexity inflates project costs, as vendors pass these costs on. - Focusing on Content Instead of Service Capability:
There is a widespread misconception that large content libraries are inherently suitable. Little attention is paid to service quality or the provider’s support capabilities. - Treating Awareness as a Compliance Checkbox:
Projects are often driven by compliance or certification needs rather than a commitment to behavioral change. This results in weak alignment with strategic goals, low motivation, and insufficient leadership.
Conclusion
Awareness success doesn’t just hinge on the provider and its products. Bigger organizations must:
- Have the right mindset. One-size-fits and plug-and-play don’t work.
- Treat security awareness as a cross-functional program.
- Invest in planning, ownership, and resource allocation.
- Define metrics beyond phishing statistics.
- Validate content and fit for audience, culture, and business. But also assess the providers capacity for adoption and customization.
- Build capacity – not just tick boxes for audits.
- Select an awareness ecosystem not only a product. If you want to know more, then check out this article: https://www.linkedin.com/pulse/key-weaknesses-cybersecurity-awareness-providers-what-palo-stacho-altoe/?trackingId=EugueCgrRr%2But67LdFZ13w%3D%3D
We’re excited to share more cybersecurity insights, news, and updates with you in the upcoming editions of this newsletter. However, if you don’t find this helpful, we’re sorry to see you go. Please click the unsubscribe button below.