Risk Attitude vs Risk Behavior: Are You Training the Wrong Thing?
Awareness ≠ Behavior
Despite comprehensive security awareness training, many organizations still continue to have cybersecurity breaches resulting from human error. We believe that it is because many people understand cybersecurity threats in theory but struggle to apply the knowledge in practice consistently to act safely.
This gap between risk attitude (knowing what is risky) and risk behavior (actually acting securely) is what today’s article will be about 😉
Risk Attitude vs. Risk Behavior in Cybersecurity
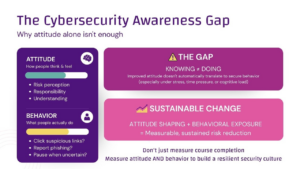
“Knowing” vs. “doing” in security are not the same.
Cyber risk attitude refers to the knowledge, awareness, and intentions of a user in relation to security (e.g. being aware that it is dangerous to click on unfamiliar links), whereas cyber risk behavior refers to the actual actions of the user (e.g. clicking on an unfamiliar link in spite of this).
A persistent attitude-behavior gap in cybersecurity has even been documented by research. Even if users are cautious, they can still be successfully attacked. This disparity is highlighted in a 2024 industry report: Even though 71% of users who took risks were fully aware of the risks, 96% of them still chose to take them [1]. To put it another way, most people acted insecurely even though almost everyone knew better. In short: they “know” but they “don’t do”.
Crucially, raising people’s awareness or concern does not automatically lead to safer action. According to one study of cybersecurity culture, “training can teach staff how to act more securely, [but] this is sometimes not enough to encourage actual secure behaviours. Knowing what to do is required but is insufficient.”.
People may truly want to behave securely and score highly on security attitude surveys or trainings, but catch themselves fumbling under pressure of stress or enticed by a well-crafted phishing email. Phishing/Smishing/Vishing/etc susceptibility is mainly an example of this intention-behavior lag: people may be able to state with assurance that they can spot a phish, but real-world click rates remain uncomfortably high. So, organizational challenge is how to bridge this gap and turn security awareness into actual secure actions.


Would You Rather:
We’ll share the results of this poll in the next newsletter – curious to see what you choose 😉
Why Traditional Awareness Training Often Falls Short?
Fundamentally, conventional awareness programs (annual slide decks, quizzes, and generic phishing emails sent to all staff) often do not replicate the pressure and personalization of real attacks. They may raise knowledge levels, but they don’t reliably change behavior.
Humans are creatures of habit and context: if training is infrequent, not targeted, or too far from users’ daily reality, its lessons fade quickly. Factors like workplace stress, fatigue, or the perceived urgency of tasks can easily override the memory of a training module from months ago . This is especially true in high-stress environments (e.g. healthcare) where staff may know the rules but, amid constant pressure, revert to insecure practices that seem expedient.
Saying it simply, one cannot lecture or quiz their way out of phishing risk – new methods are needed to actually influence day-to-day user actions.
A New Approach: Personalized, Context-Aware Phishing Simulations in Combination With Customized E-learnings!
Most phishing training still looks way different from real attacks. It’s generic, predictable, and easy to detect. But real threats? They’re personalized. They use names, roles, company context—whatever makes the message feel real.
Attackers often use publicly available information to craft these emails. So it makes sense that training should do the same. When a simulation feels believable, users react the way they would in real life – not the way they think they should in a quiz. Remember the cyber risk behavior right?
In light of these insights, new solutions are arriving to help organizations implement personalized phishing training at scale. For example, our OSINT Reconnaissance Module *** – a newly announced feature. It is designed to automate the generation of highly realistic phishing simulations using publicly available data. This kind of tool can continuously scour open sources to tailor fake phishing emails to each employee with the help of of our phish-email-automator (e.g. referencing a recent social media post or a public company announcement), operationalizing the research-backed principle that the more realistic and targeted the simulation, the more effective the learning outcome. By leveraging automation and intelligence, such a module allows security teams to run ongoing, adaptive phishing exercises without massive manual effort – an important factor for scaling and adoption of the cybersecurity awareness solution. The end goal is to create a self-improving “human firewall”: employees who not only know about phishing but have practiced their responses to the point of habit.
*** The OSINT Reconnaissance Module is available as an experimental feature since Version 2.7.0. If you’d like to explore it further or activate it for your team, feel free to reach out or check the release notes in your dashboard.
Due to the growing experience of customers and because of the emergence of AI: Cybersecurity awareness programs are evolving from checkbox compliance exercises to tailored, culturally-sensitive, technically-integrated solutions. By actively avoiding the pitfalls identified above and insisting on modern, AI-enabled solutions that align with operational realities, companies can meaningfully improve human-layer security.
[1] https://www.proofpoint.com/us/blog/security-awareness-training/2024-state-of-phish-report
We’re excited to share more cybersecurity insights, news, and updates with you in the upcoming editions of this newsletter. However, if you don’t find this helpful, we’re sorry to see you go. Please click the unsubscribe button below.