Which cyber training has the greatest learning effect?
Published Date:
- January 23, 2024
It is now undisputed that a Cyber Attack has become one of the biggest and most costly threats to companies. A secure technical infrastructure is often no longer sufficient, as well over 60% of all hacker attacks are phishing attacks that target human vulnerabilities [1]. These so-called “social engineering” attacks are also becoming increasingly sophisticated. According to a survey, 52% of companies stated that phishing attacks became more sophisticated in 2023 [2].
To keep this security gap to a minimum, the security awareness of employees should be trained with more individualized measures than is currently possible with the standard training offered by most established providers. Employees must be able to recognize when an email is a phishing email and when it is not, even in sophisticated attack scenarios.
So how can employees be trained in the best possible way to recognize Cyber Attacks in good time and protect the company?
Of course, targeted cyber training in the form of e-learning formats is a good way to do this. In this article, we get to the bottom of the question of which formats are most effective and achieve the greatest learning effect.
The different e-learning formats
In the digital age and especially since the advent of artificial intelligence and chatbots, the way we learn has changed. Why should we spend ages poring over books when the answer can be visualized in an entertaining and appealing way, presented digitally, or asked with the help of a chatbot?
Digital learning formats range from videos and games to the AI chatbots. The content of many formats can often be adapted to the needs of the user and put together individually. And you should do this, because conveying the learning content in the context of the learner and its organization is one of the keys to sustainable learning success.
Here we provide a brief overview of the best-known learning formats and their application in the field of cyber training:
A. Learning Videos
Cyber security learning and training videos should be short and concise to keep learners’ attention. Ideally, they should be no longer than three minutes, unless the content requires more detailed consideration. In such cases, it is important to make the video entertaining to keep viewers engaged. The style of the video should match the content and strike a balance between entertainment and education. Complex topics need a calm, focused approach, while longer or drier content should be enriched with engaging visuals and narration to maintain interest.
Here is an overview of the most popular video styles in the cyber training context:
- Digital animation is popular in educational videos and its versatility is particularly suitable for cyber training, suitable for all ages and content. These videos can be used cross-culturally and multilingually as they simplify complex topics and convey knowledge in an entertaining way. Depending on your needs, animated videos can be simple or colorful to minimize distractions or make dry content livelier.
For example, complex content can be kept black and white to keep distractions to a minimum, while more elements and colors can be used to convey dry content. - Whiteboard animation videos use markers and whiteboards to present learning content visually and explain it with an audio track. This method focuses on the essentials and promotes understanding of complex topics. In addition, such videos are usually cost-efficient and easy to produce. This means that individual adaptations can also be made easily and inexpensively.
- The comic or cartoon style is very popular and makes learning content entertaining but can sometimes be perceived as less serious. However, it makes sense to include such videos in the training catalog, you should not commit to a single style.
- Live action videos: Live-action videos with human actors enable a realistic presentation of content but are often time-consuming and cost-intensive to produce. AI will not be able to change this fact in the medium term. Furthermore, live action videos are often longer, and this can lead to the available training budget per employee and the reserved time resources being exceeded.
- Interactive videos combine learning units with game and quiz elements and offer users the opportunity to help shape the video experience by answering questions and making decisions. This format increases concentration and enjoyment of learning through active participation and repeated knowledge control. Thanks to its effectiveness and user engagement, it is often seen as a pioneering approach to digital learning.
This method is very popular in cyber security awareness training (SAT). On the one hand, quiz questions can be adapted based on context and, on the other, they can be used to test what has been learned. For example, in cyber training, the video can first explain what the characteristics of a hacker scam are, and this knowledge can then be tested in a quiz.
Interactive videos are a specialty of Cyberdise and are often used in Cyberdise security awareness training courses due to their high entertainment factor and learning effect.
B. Quiz
Quizzes are a form of game-based learning in which the participants’ knowledge is usually tested with multiple choice options. A quiz often follows a learning block to test what has been learned previously or at the beginning and after completion of the overall training to measure the success of the training.
For example, the Cyberdise Phishing Quiz tests participants to see whether they recognize a phishing email or, if necessary, whether they incorrectly identify a normal email as a phishing email. Company-specific adjustments can also be made.
C. Cybersecurity Chatbots
Cybersecurity chatbots allow learners to independently request information about security and cybersecurity guidelines. The fact that individual questions and answers are given in normal colloquial language raises the learning effect to a considerably higher level.
It is important that the chatbot provides answers based on the company’s security guidelines. Otherwise, it makes no sense, as the aim is not to provide general information, but company-specific information!
Our experience shows that the learning effect is highest with chatbots due to the high level of interactivity and individuality. Cyberdise offers a configurable cybersecurity chatbot for security awareness training and for employees that makes exactly this possible.
D. Standard or customized cyber training?
In the field of e-learning, especially in security awareness training, a distinction is mainly made between standardized and customized content. While standardized content is designed for a broad target group and does not require any special adaptations, individually tailored content is necessary for specific company or industry requirements. Tailor-made cyber training makes it possible to train employees in a targeted manner, for example in recognizing phishing scams, whereby the training materials should be adapted to the company’s specific systems and processes.
The demand for individual training is not only increasing among large companies, as specific company guidelines and procedures often need to be integrated into the training. For example, the desire is often expressed to embed company-specific content in standard courses such as ‘secure password use’.
E. Monitoring learning outcomes and reporting
Tracking learning outcomes is a critical aspect of using e-learning programs. It is essential to record the level of knowledge of participants before training begins and to continuously assess it throughout the course to measure the progress and effectiveness of the training. Progress monitoring systems make it possible to track the learning process and motivate participants through visible success. It is also a method for companies to evaluate the return on investment of their training measures.
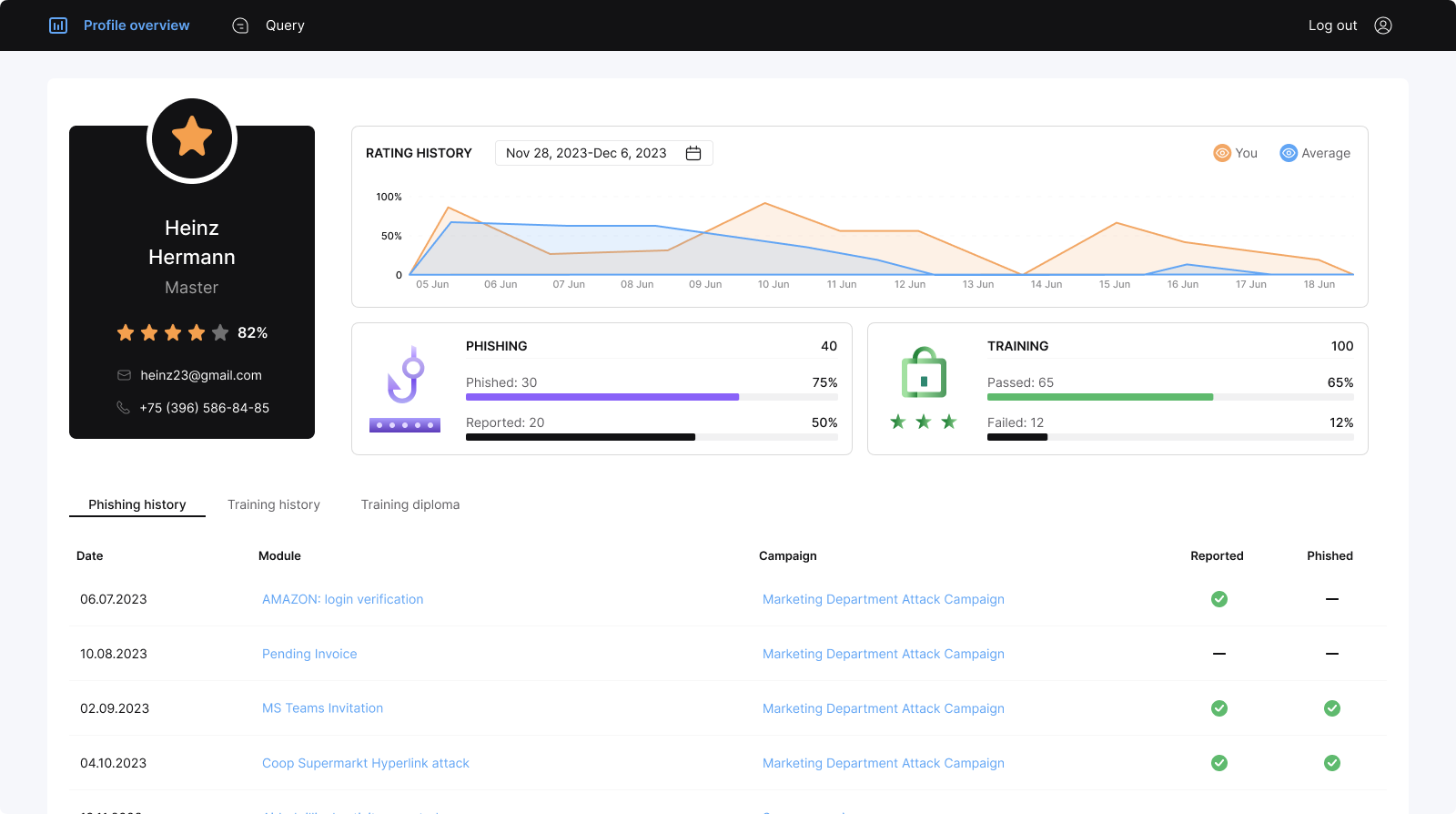
The security awareness of employees is tested at the beginning of the security awareness training using various simulated Cyber Attacks, such as phishing or smishing simulations. Their progress is then measured over time: to what extent are employees aware of Cyber Attacks and able to recognize them?
Cyberdise makes it very easy to measure awareness and learning progress and to check learning success. Attack statistics and learning progress can be tracked in real time and over time. You can also track attack simulation statistics such as the number of emails opened, the number of links clicked and successful attacks.
Weaker employees are automatically identified and can be assigned to special training programs for people with lower skill levels.
You can find more information at cyberdise-awareness.com