Key Weaknesses of Cybersecurity Awareness Providers and What Companies Can Do About Them
Published Date:
- June 25, 2025
Cybersecurity awareness training is a vital component of organizational defense strategies. However, many awareness providers or solutions are not able to cover the requirements of the customers. We list and summarize common weaknesses of security awareness providers and practical steps (bigger) organizations can take to address them.
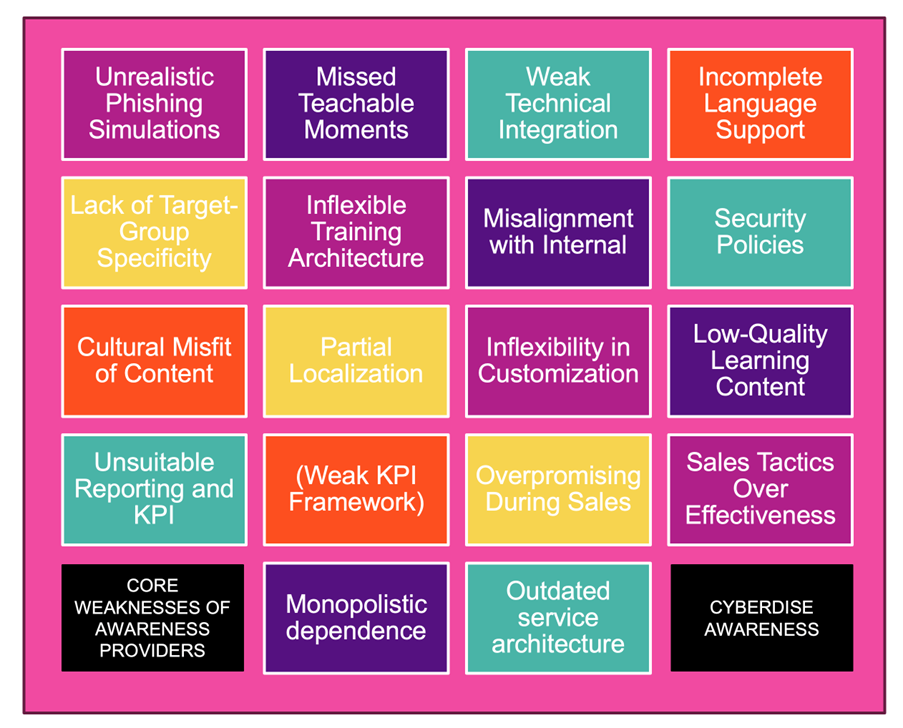
- Unrealistic Phishing Simulations
- Missed Teachable Moments
- Weak Technical Integration
- Incomplete Language Support
- Lack of Target-Group Specificity
- Inflexible Training Architecture
- Misalignment with Internal Security Policies
- Cultural Misfit of Content
- Partial Localization
- Inflexibility in Customization
- Low-Quality Learning Content
- Unsuitable Reporting and KPI (Weak KPI Framework)
- Overpromising During Sales
- Sales Tactics Over Effectiveness
- Monopolistic dependence
- Outdated service architecture
1. Unrealistic Phishing Simulations
Problem: Simulations are overly simplistic and lack technical realism, reducing training value.
Solution: Look out for a provider which is able to provice context-aware, dynamic phishing simulation templates that reflect real-world attacker behavior. Also check it’s ability that the provider is to provide custom simulation attack scenarios for your particular needs. Investigate if the provider has internal. service processes in place to provide such attack and training content.
2. Missed Teachable Moments
Problem: After clicking on simulated attacks, users don’t get, skip or ignore the intended learning interventions.
Solution: Ensure that training modules trigger can be immediately delivered after user actions, with engaging and interactive content. Assess also the posibility if these teachable can be delivered multiple times by the system on request (For example immediately and a second time 10 minutes later via email)
3. Weak Technical Integration
Problem: We often see that customers often evaluate only integration mechanism and and not consider that such processes can change and evolve. The just look to manual user data import and underestimate API support.
Solution: Prioritize platforms offering strong API and directory integration (e.g., LDAP, Entra, AD) for seamless user management. Investigate solutions that are able to manage user synchronizations with CSV uploads as well.
4. Incomplete Language Support
Problem: Modules often lack full translation or rely on poor-quality subtitles or automated translations.
Solution: Use providers that able to provide native, high-quality translations and support for full localization of all interfaces and content. Watch out not for the amount of languages but for the ability of the provider to do the translations easily, swiftly and on an affordable basis. Check whether the underlying software solution offers the option of doing the translations yourself, in which case customers can do it themselves or commission someone else to do it.
5. Lack of Target-Group Specificity
Problem: Generic content fails to address the distinct needs of different roles (e.g., IT, HR, data protection officers).
Solution: Check out if role-based or user-maturity-specific training curriculums are available with the option to tailor the modules so that they reflect actual job functions and responsibilities. Don’t expect that the provider has training content absolutely matching your context but asses it’s ability if he’s able to adopt it easily. Choose a provider who includes software functionality which would allow you to do it yourself. This means you retain control over your requirements and are not dependent on the provider.
6. Inflexible Training Architecture
Problem: Due to any kind of reasons the awareness training materials and simulations need to be distributed across disparate platforms, even if they are a source for user fatigue and inefficiency.
Solution: Choose a provider who offers a flexible solution that one hand integrates learning management, phishing simulations, and reporting functions on one instance or multiple tenants. On the other hand the solution and the providers services should also support decentralization if needed, so that attack simulations might be conducted from multiple instances and tenants or trainings might be exported (SCORM) to 3rd party LMS. All of this should be possible without hindering the consolidation of reporting on the respective awareness-raising activities and measures.
7. Misalignment with Internal Security Policies
Problem: Security advice given in training contradicts an organization’s own IT guidelines.
Solution: Organizations have to adjust their expectations from ‘provider has the right training for me out-of-the-box. Make sure that the provider or the platform is able to deploy customizable training content that are adjusted and aligned with internal policies and updated as policies evolve. Assess if the provider allows the adoption by yourself or if the provider is mastering an efficient and affordable deployment process for individualization, localization and content customization.
8. Cultural Misfit of Content
Problem: Content designed for one region (e.g., “too American” ot “only Western avatars”) may not resonate with global users.
Solution: Assess the providers ability not just translating the language, but also the tone, visuals, and scenarios to reflect diverse cultural norms. Watch out not for the amount of multicultural content but for the ability of the provider to do requested adoptions easily, swiftly and on an affordable basis. Check whether the underlying software solution offers the option of managing the cultural adoption yourself, in which case customers can do it themselves or commission someone else to do it. And last but not least check if multicultural awareness content can be imported and exported by yourself
9. Partial Localization
Problem: Some modules are only available in English and some other major languages, undermining training in multilingual organizations.
Solution: Opt for solutions and providers that support full localization, including user-defined language additions. Check out if you could do it yourself in the platform, this gives you freedom of action when needed.
10. Inflexibility in Customization
Problem: Platforms lack agility to accommodate organization-specific needs or content.
Solution: Choose providers that allow deep and even bulk customization—of modules, branding, curriculums, training sets/paths and rating levels.
11. Low-Quality Learning Content
Problem: Content is perceived as boring, generic, generated purely with AIor overly simplistic.
Solution: Invest in high-quality, professionally produced content with interactive formats (e.g., quizzes, videos, gamification). Start relying more on customized content than on a large standard library with poor quality. Look for solutions and vendors that support such a service paradigm in a cost-effective way, even for many languages and multicultural organizations. Old content does not necessarily have to be bad, but pay attention to current cybersecurity training (2025 and newer).
12. Unsuitable Reporting and KPI
Problem: Reports are not fitting or can’t be adopted. The KPI framework is weak or misleading: Metrics like “click rate” or “report rate” are often misleading or insufficient.
Solution: Implement platforms with comprehensive analytics and reporting API that track behavior change, training completion, and risk exposure. Don’t expect unlimited reporting and analysis options from awareness providers, but rather the ability to integrate awareness results into your own analytics platforms. Last but not least, check whether the provider also has professional tools for measuring employee awareness, such as scientifically based awareness surveys or ‘awareness for awareness’ tests/quizzes/exams.
13. Overpromising During Sales
Problem: Vendors promise future features that are delayed or never delivered.
Solution: Demand clear, transparent feature documentation and confirm (future) availability before procurement. And nobody forbids you to include your desired future requirements as part of the service contract. You will find out very quickly if the awareness provider is open to such kind of agreements. Clarify such requests at the beginning of the evaluation, if you do this in the final procurement process, its too late.
14. Sales Tactics Over Effectiveness
Problem: Bundled sales models push unsuitable platforms based on price rather than value.
Solution: Evaluate awareness providers and solutions based on fit-for-purpose criteria and adoption possibilities, not bundling incentives.
15. Monopolistic Dependence / Single Vendor Approach
Problem: You only evaluate various platform providers that have no or a weak service partner landscape. Or service partners are selected who pass on the services to the product/platform operator without generating significant added value for the organization. This leads to a provider lock-in, where you cannot change suppliers without having to change the technology and/or system architecture.
Solution: Evaluate awareness providers who offer their services on an open product that is also accessible to third-party providers (awareness ecosystem). Alternatively, decide not to evaluate SaaS platforms that only offer direct sales. As an organization, you retain the option of changing suppliers without changing the entire awareness program or the underlying platform. You retain the freedom to change and the awareness vendor is aware of this, which in our experience is often a very good basis for a good long-term collaboration.
16. Outdated Service Architecture
Problem: The software and content architecture is that of a first- or second-generation awareness product or platform. Modifications and customer-specific adaptations are only possible with significant effort. Maintenance of existing content is not automatic or is associated with high manual effort and costs. The provision of new features is slow and comes late. The solution is not AI-native, a serious shortcoming that will have a massive impact in the future in view of the shortage of cybersecurity personnel, because the huge potential for efficiency through the use of AI cannot be leveraged.
Solution: Make sure that the offerings of cybersecurity awareness providers are based on a 3rd generation awareness software stack: AI-native; fully editable and customizable, automated, multi-channel capable, open and integratable.
Due to the growing experience of customers and because of the emergence of AI: Cybersecurity awareness programs are evolving from checkbox compliance exercises to tailored, culturally-sensitive, technically-integrated solutions. By actively avoiding the pitfalls identified above and insisting on modern, AI-enabled solutions that align with operational realities, companies can meaningfully improve human-layer security.
Experience and Scientific Evidence
Our team has been building awareness solutions and software for small, large and even global customers since 2015. Our experience has been incorporated into a completely new third-generation product, which has been on the market since 2023.
The experience we share here is supported by a number of scientific papers, including the somewhat older USENIX study “To Do This Properly, You Need More Resources” from 2022/23 and scientific papers on AI (2024 and 2025)
- The Hidden Costs of Introducing Simulated Phishing Campaigns https://www.usenix.org/system /files/usenixsecurity23-brunken.pdf
- Evaluating Large Language Models’ Capability to Launch Fully Automated Spear Phishing Campaigns https://arxiv.org/abs/2412.00586
- AI-Enabled Spearphishing Simulations – https://www.hslu.ch/en/lucerne-university-of-applied-sciences-and-arts/research/projects/detail/?pid=6700