Is it Europe’s Largest InfoSec Show and Why Should It Matter to You?
Did you know that it-sa Expo & Congress in Nuremberg is one of Europe’s leading cybersecurity events? This year, it set new records with 25,830 trade visitors from 65 countries and 897 exhibitors. This gathering of experts in Nuremberg brought together the best minds to tackle today’s biggest threats and newest defense strategies. We’ve sifted through the highlights to bring you practical, actionable insights that can make a real difference in your organization’s IT security. From awareness training to protecting critical infrastructures, here are the takeaways, complete with statistics and strategic advice.
Awareness: Building the First Line of Defense
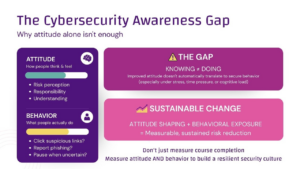
Human error remains a major vulnerability in cybersecurity, with an estimated 90% of incidents linked to mistakes made by employees. Interestingly, younger employees (18-40) are shown to be 65% more likely to click on phishing links than their older counterparts, suggesting that awareness training needs to adapt to different demographic behaviors(1).
At it-sa 365, experts stressed the importance of dynamic, scenario-based training to help employees at all levels recognize phishing attempts, manage passwords securely, and become active participants in defending against cyber threats. An engaging, tailored approach to awareness can dramatically reduce the likelihood of successful phishing attacks and other social engineering threats.
OT Security: Protecting Industrial Operations
Operational Technology (OT) is essential in industries like manufacturing, healthcare, and energy, yet it’s highly susceptible to cyber risks due to its reliance on legacy systems and proprietary protocols. In fact, 70% of OT professionals report at least one breach annually, highlighting the critical need for specialized security (2).
Effective OT security strategies discussed at it-sa 365 include adaptive network segmentation to limit the reach of any breach, and customized patch management to keep even older systems as secure as possible. The message was clear: OT environments require solutions that don’t disrupt essential operations but can still mitigate risk.
Network & Application Security: Securing Digital Infrastructure
The expansion of IoT and remote work has increased network vulnerabilities, and by 2025, 60% of enterprises are expected to transition from traditional VPNs to Zero Trust architectures (3). This shift highlights the importance of treating every access request as potentially hostile, requiring continuous verification.
Zero Trust and strong application security were focal points at it-sa 365, with recommendations to secure applications from development through deployment. By incorporating robust access controls and employing tools like Public Key Infrastructure (PKI), companies can strengthen their digital foundations, ensuring that both users and data are continually authenticated and monitored.
Data Center Security & Identity Access Management (IAM): Ensuring Comprehensive Access Control
Data centers are a critical point of vulnerability, with the average cost of an outage reaching over $600,000. At it-sa 365, speakers emphasized the importance of advanced Identity Access Management (IAM) systems to regulate user access and enforce stringent authentication protocols across systems (4).
IAM was presented as a cornerstone of data center security, helping to control both physical and digital access while ensuring that only verified users can reach sensitive systems. Effective IAM, combined with physical safeguards, is essential for protecting an organization’s most valuable assets against unauthorized access.
Cloud Security: Navigating a Complex Threat Landscape
As over 90% of organizations now rely on cloud solutions, cloud security has emerged as a priority – but one that many struggle to manage effectively (5). The complexity of hybrid and multi-cloud environments often leads to inconsistent security policies, which can create dangerous gaps.
Experts at it-sa 365 recommended layered security approaches for cloud environments, including encryption, endpoint protection, and strict access controls. Building a unified security framework across all cloud services can help organizations secure their data while maintaining the flexibility that cloud solutions provide.
Critical Infrastructures (KRITIS): Ensuring Resilience in Essential Sectors
Critical infrastructures – sectors such as energy, healthcare, and finance – are foundational to societal stability, making them frequent targets of sophisticated cyber threats. Attacks on these sectors increased by 50% last year in the EU, underscoring the urgent need for robust security protocols (6).
At it-sa 365, compliance with updated standards like the IT Security Act was emphasized as essential, but experts also advised going beyond compliance to conduct regular risk assessments and implement incident response plans. These steps help critical infrastructure operators anticipate threats and build resilience, ensuring that essential services continue uninterrupted.
Hacking & Defence: Proactive Measures for a Changing Threat Landscape
With cyberattacks becoming increasingly sophisticated, especially in areas like ransomware (which saw a 62% increase last year), proactive defense is no longer optional. it-sa 365 highlighted the importance of multi-layered defense strategies, from firewalls and intrusion detection systems to VPNs and Security Information and Event Management (SIEM) tools (7).
Preparation was also a key theme, with experts urging companies to develop incident response plans that allow quick recovery from breaches. Regular penetration testing and continuous monitoring can expose vulnerabilities before attackers do, helping organizations stay one step ahead of potential threats.
At this year’s it-sa Expo & Congress, we surprised visitors with the launch of Cyberdise’s Freemium edition. This free offering addresses common security challenges of the Human Factor with innovative solutions, showcasing our advancements over traditional methods. The Freemium edition is also available to you!
1. it-sa 365 | Topic: Awareness. (n.d.). Itsa365. https://www.itsa365.de/en/news-knowledge/topics/awareness
2. it-sa 365 | OT Security. (n.d.). Itsa365. https://www.itsa365.de/en/news-knowledge/topics/ot-security
3. it-sa 365 | Network & Application Security. (n.d.). Itsa365. https://www.itsa365.de/en/news-knowledge/topics/network-application-security
4. it-sa 365 | Data Center Security & Identity Access Management. (n.d.). Itsa365. https://www.itsa365.de/en/news-knowledge/topics/data-center-security-iam
5. it-sa 365 | Cloud Security. (n.d.). Itsa365. https://www.itsa365.de/en/news-knowledge/topics/cloud-security
6. Critical Infrastructures (KRITIS). (n.d.). Itsa365. https://www.itsa365.de/en/news-knowledge/topics/kritis
7. it-sa 365 | Topic: Hacking & Defence. (n.d.). Itsa365. https://www.itsa365.de/en/news-knowledge/topics/hacking-defence