Are You Sharing Too Much Online? The Cyber Risks You Overlook - Lessons From "Carry-On”
Published Date:
- January 22, 2025
What "Carry-On" Teaches Us About Cybersecurity Threats?
While “Carry-On” primarily focuses on physical security in an airport, its themes resonate deeply with today’s cybersecurity challenges. To us, the movie serves as a stark reminder of how vulnerabilities – both technological and human – can be exploited with devastating consequences. Let’s explore key moments:
1. Human Psychology is the Weakest Link
In the movie: The protagonist’s fear and desperation are exploited by the antagonists. They use his personal struggles – financial issues and family concerns – as leverage to make him
comply.
The real-world connection: Social engineering relies heavily on manipulating human emotions like fear, urgency, or trust. Phishing emails that threaten account closures or promise rewards operate on the same principle.
→ Lesson: Always pause and think critically before responding to unexpected or
emotionally charged requests. You have to remember: “I am the target”.
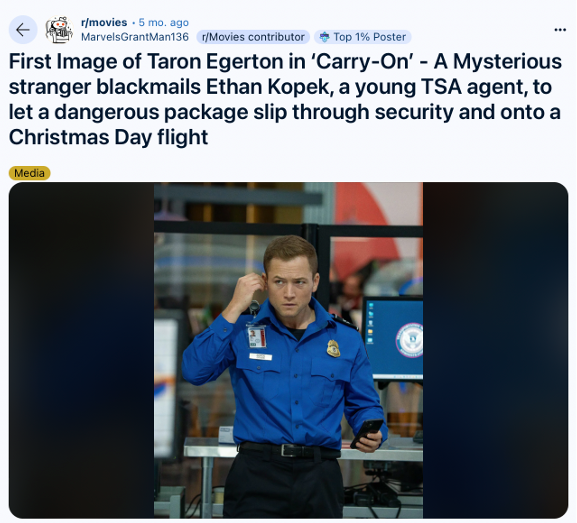
2. Hackers Could Use Everything You Share Online
In the movie: When the TSA officer unexpectedly takes over a place, the hackers
immediately shift gears. Within moments, they pull up everything they need about him from publicly available sources, manipulating him with precision.
The real-world connection: Cybercriminals use open-source intelligence (OSINT) to build
profiles on individuals. From LinkedIn job details to personal habits on Instagram, they piece together information to exploit their targets.
→ Lesson: Be mindful of the data you share online. Even seemingly harmless posts can
become tools for attackers. And use Cyberdise’s OSINT capabilities for training your staff.
Scene from a movie showing how easy it is to find information about people online [1,2].
3. Surveillance as a Tool of Control
In the movie: The hackers somehow discover that the police officer is investigating the case
and could stop their plans. By tracking her location, monitoring her activities, they manipulate her movements and divert her focus, trying to make her abandon the investigation and follow a false lead instead.
The real-world connection: This mirrors how attackers use GPS tracking, spyware, and even compromised apps to monitor victims. Such surveillance can lead to targeted attacks or extortion.
→ Lesson: Regularly review app permissions, disable unnecessary tracking, and use
security tools to keep your infrastructure non-compromised from spyware etc.
4. Resilience in Security Systems Matters
In the movie: A single compromised decision leads to a chain reaction, exposing vulnerabilities across the airport’s entire system.
The real-world connection: A similar scenario can happen in workplaces. One employee clicking a phishing link or using a weak password can open the door to cybercriminals, leading to a data breach that costs the company millions in fines, lost revenue, and reputational damage.
→ Lesson: Protect your organization by using strong, unique passwords, enabling multifactor authentication, and verifying suspicious emails or requests before acting. If you are responsible for cybersecurity awareness, constantly run phishing simulations and trainings.

How “Carry-On” Would Have Ended in 10 Minutes if the Airport Had a Solid Security Culture and Awareness?
1 Strong Cybersecurity Shut Hackers Out
In the movie: The attackers exploit weak access points to infiltrate airport systems.
What should’ve happened: With mandatory cybersecurity checks, their attempts would’ve hit a dead end.
2 No Oversharing, No Leverage
In the movie: Hackers gather personal information about the protagonist to manipulate him.
What should’ve happened: A cybersecurity culture discouraging oversharing online means they have no leverage to exploit.
3 Staff Spot The Phishing Attempt
In the movie: The hackers gain access to critical systems through deceptive means.
What should’ve happened: Regular phishing simulations and training enable staff to identify
and block the threat before it escalates.
4 Incident Response Shuts It Down Fast
In the movie: A single decision spirals into a full-blown crisis.
What should’ve happened: A robust incident response plan isolates the threat immediately, preventing a chain reaction.
5 Be Prepared For The Unprepared
In the movie: The attackers adapt quickly to unexpected changes, finding new ways to
exploit the situation and stay ahead. On the contrary, the main characters struggle to act
effectively in this very unpredictable situation.
What should’ve happened: Awareness training should prepare staff for dynamic,
unpredictable scenarios. Cybersecurity isn’t about sticking to the plan – it’s about staying flexible and thinking critically when the unexpected happens.
CYBERDISE Got Better: See What’s New
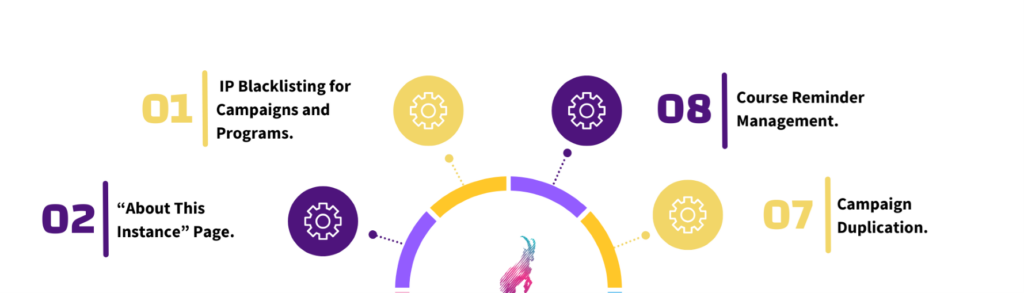
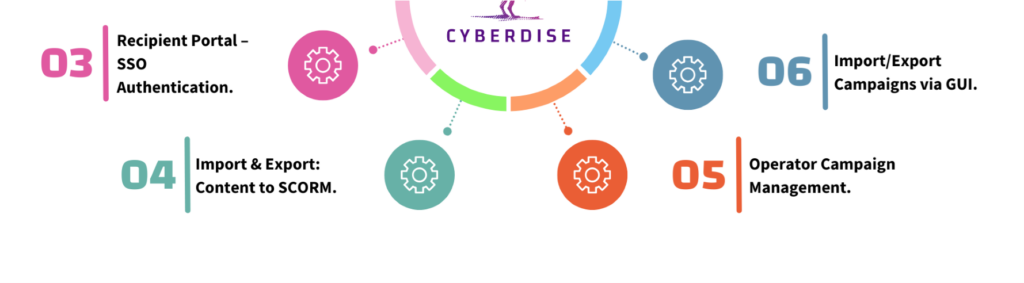
Read in a more detail: https://cyberdise-awareness.com/release-note/
You think you know someone well enough to phish them? Try CYBERDISE Freemium - completely free phishing simulation tool
Try it out – but not for real, of course! Instead, challenge your friends, family, or employees with a simulated phishing email. You might be shocked at how easily even the savviest among us can fall for a cleverly crafted attack.
With Cyberdise Freemium Edition, you can fully customize phishing simulations to fit your context, helping your team learn to spot and stop threats before they escalate. It’s easy, effective, and even a little fun.
New in Freemium! Now, you can export your campaigns and import them into another Freemium instance.