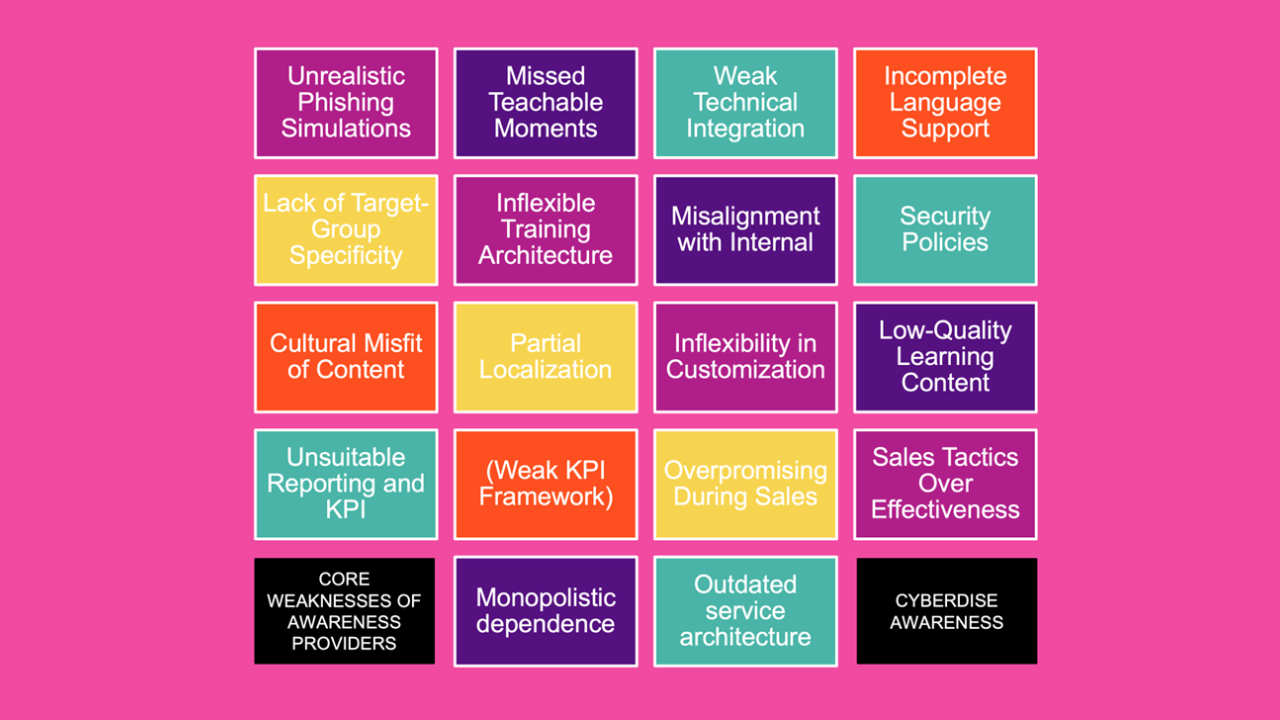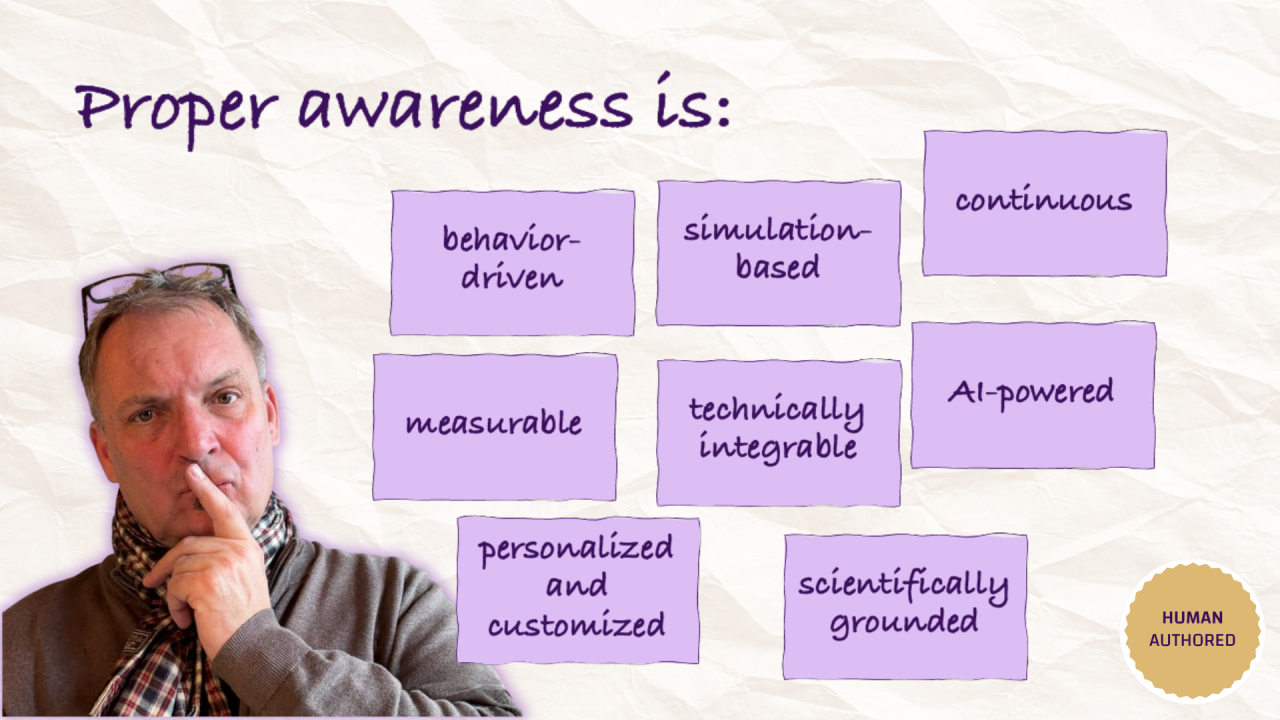
What is Proper Awareness?
An entire industry often offers customers products and services with little benefit. And they even buy into it!
Today in 2026, the cybersecurity awareness market will be worth around USD 6.7 billion [1]. Created just over 20 years ago, it is dominated by awareness or SAT providers, which I regard to be second generation. Companies such as Proofpoint, Terranova, Knowbe4, Sans, Sosafe, Hoxhundt, or whatever they are called, secure the lion’s share of this market, which is expected to grow to just under USD 15 billion in 2031. In addition, there are hundreds of other players, such as CYBERDISE | Cybersecurity Awareness .