Why Security Awareness Will Always Work – If You Build and Measure the Right Thing
Published Date:
- January 12, 2026
Recent discussions around the effectiveness of cybersecurity awareness have been reignited by high-profile media coverage. Most prominently, a Wall Street Journal article drawing on the study “Understanding the Efficacy of Phishing Training in Practice” questions whether phishing simulations and awareness training lead to meaningful risk reduction.
The debate itself is healthy. The conclusions drawn from it, however, require more nuance.
A growing body of empirical research shows that well-designed cybersecurity awareness programs do improve real-world cyber risk behavior. What often fails is not awareness as such, but narrow interpretations of what awareness is, how it should be embedded organizationally, and how success should be measured.
Cybersecurity Awareness Is Not a Standalone Control
Effective protection against phishing and social engineering does not emerge from isolated training campaigns. It is the result of a vibrant cybersecurity culture combined with robust cybersecurity governance. In mature organizations, awareness is one element of a broader socio-technical system that includes:
- Clear governance structures and accountability
- Consistent policies and enforcement
- Secure-by-design technical controls
- Incident reporting and feedback mechanisms
- Continuous risk communication
Well-designed and intelligent cybersecurity awareness activities are a key enabler of this system, but they are not the system itself.
Training modules and phishing simulations are therefore best understood as tools, not solutions. Their purpose is to shape perception, reinforce norms, and — crucially — expose employees to realistic risk in a controlled environment. When integrated into governance and culture, they amplify organizational resilience. When treated as checkbox exercises, they decay into compliance theater.
The Core Analytical Error: Confusing Attitude with Behavior
Many critical assessments of awareness programs implicitly assume a linear relationship:
Knowledge → Awareness → Secure behavior
Behavioral research shows that this assumption does not hold — particularly in cyber contexts.
Empirical studies consistently find that:
- Training primarily influences attitude and risk perception
- Exposure to realistic threats influences actual behavior
- The correlation between attitude and behavior is weak
This distinction is fundamental. Measuring awareness effectiveness via survey responses or short-term click rates conflates psychological constructs that behave very differently under real attack conditions.
A Nuanced View on the WSJ-Referenced Study
The study “Understanding the Efficacy of Phishing Training in Practice” is methodologically sound, carefully executed, and intellectually honest. It deserves recognition for its rigor and transparency.
However, two limitations substantially relativize its broader conclusions:
- The study only a single organization. Organizational culture, governance maturity, prior exposure, and security climate vary widely. Findings from one environment cannot be generalized to the entire awareness discipline.
- The raw data cannot be published. While understandable for understandable for confidentiality reasons, this limits independent validation, secondary analysis, and cross-study comparison – all essentials for scientific consolidation.
We understand the study as a case study, not as definitive evidence against cybersecurity awareness as a whole.
The WSJ article correctly observes that many awareness programs underperform. Its extrapolation from a narrow empirical base to a general verdict on awareness effectiveness is where the argument becomes fragile.
Across industries such as aviation, healthcare, and industrial safety, training effectiveness has long been understood as a function of design, realism, repetition, and systemic integration.
Cybersecurity is no different. What fails in practice are typically:
- Generic, low-context simulations
- Infrequent, compliance-driven campaigns
- Knowledge-heavy, experience-light training
- KPIs focused on clicks instead of behavior over time
What works are governance-aligned, behavior-focused, and exposure-driven programs embedded in a living security culture.
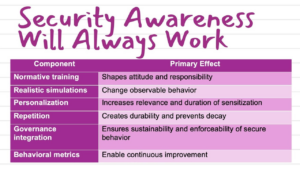
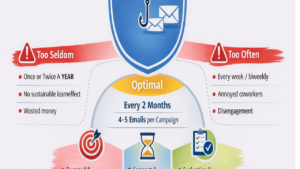
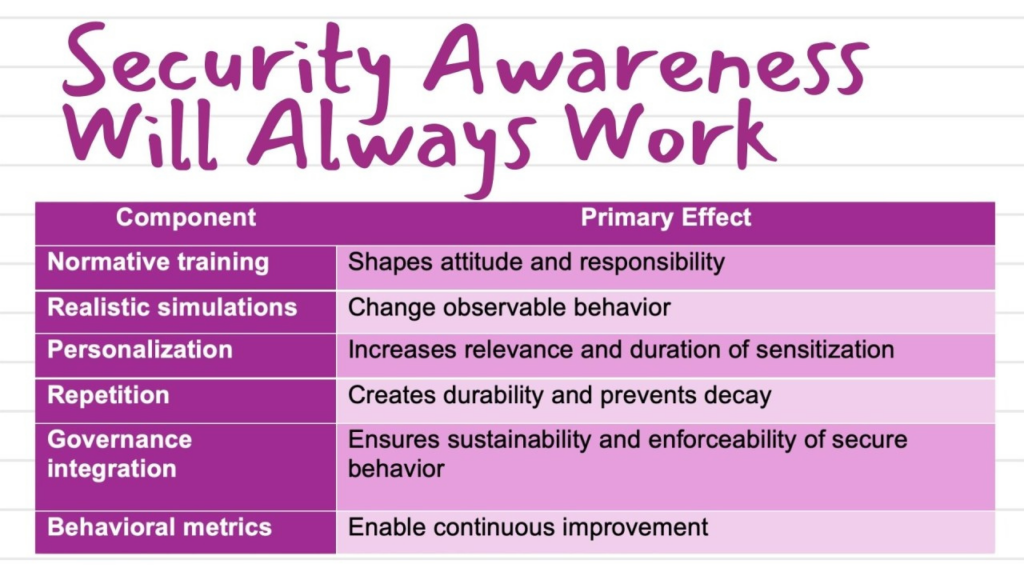
Awareness Building Blocks: A More Accurate Mental Model for CISOs
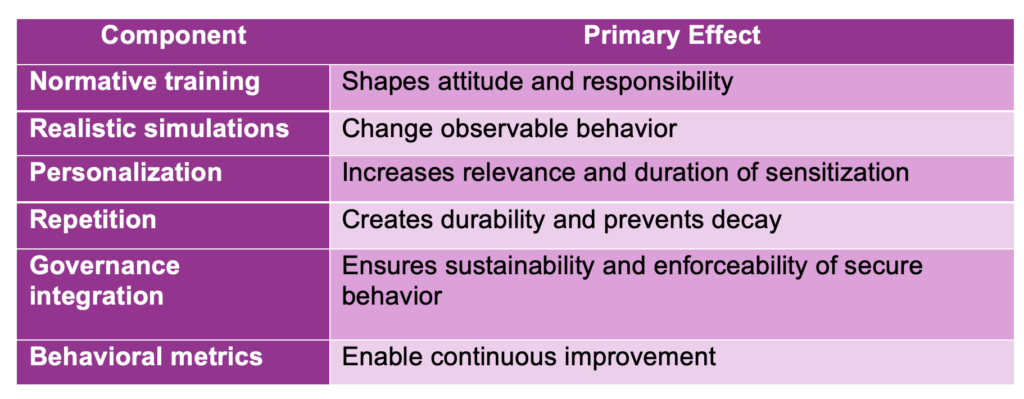
Only when these elements interact does awareness become a measurable risk-reduction mechanism, rather than a symbolic exercise.
Implications for Security Leadership
- Do not ask whether awareness works. Ask which awareness works, under which conditions.
- Embed awareness in governance and culture. Training without structure will decay.
- Measure behavior, not belief. Surveys are not a proxy for resilience.
- Assume AI-enabled attackers. Anything less trains the wrong reflexes.
- Treat awareness as a system, not a campaign.
When designed and governed correctly, cybersecurity awareness does not eliminate risk — but it measurably reduces the most exploited attack surface: human behavior.
- Do not ask whether awareness works. Ask which awareness works, under which conditions.
- Embed awareness in governance and culture. Training without structure will decay.
- Measure behavior, not belief. Surveys are not a proxy for resilience.
- Assume AI-enabled attackers. Anything less trains the wrong reflexes.
- Treat awareness as a system, not a campaign.
When designed and governed correctly, cybersecurity awareness does not eliminate risk — but it measurably reduces the most exploited attack surface: human behavior.
References
- Pugnetti, C., Stacho, P. Improving Cyber Risk Behavior through AI-Enabled Spear Phishing. Lucerne University of Applied Sciences (HSLU), 2025. https://cyberdise-awareness.com/wp-content/uploads/2025/12/4-aisp-study-AI-Enabled-Spearphishing-Paper.pdf
- Reinheimer et al. An Empirical Study on Phishing Training Decay. SOUPS, 2020.
- Heiding et al. Evaluating Large Language Models’ Capability to Launch Fully Automated Spear Phishing Campaigns. arXiv:2412.00586, 2024.
- Björck et al. Towards Diagnosing and Mitigating Behavioral Cyber Risks. Risks, MDPI, 2024.
- Ho et al. Understanding the Efficacy of Phishing Training in Practice. IEEE 2025 SP. https://people.cs.uchicago.edu/~grantho/papers/oakland2025_phishing-training.pdf
We’re excited to share more cybersecurity insights, news, and updates with you in the upcoming editions of this newsletter. However, if you don’t find this helpful, we’re sorry to see you go. Please click the unsubscribe button below.