Why Hackers Love Your Social Media - and How to Stop Them
Published Date:
- March 4, 2025

In today’s hyper-connected digital world, the information we share online is more powerful – and more dangerous – than ever. While social media and public platforms help us stay connected, they also provide cybercriminals with a goldmine of data to fuel their attacks. By exploiting details from your LinkedIn profile, Facebook posts, or even your company’s website, attackers can craft highly personalized and convincing phishing scams that are harder to detect and resist.
But how exactly do hackers use your public information, including social media, against you? And what can you do to protect yourself and your organization from these sophisticated attacks? What does OSINT stand for and why are we mentioning it here? In this article, we’ll explore how cybercriminals turn your online presence into a weapon – and share actionable tips to help you stay safe.
What is OSINT and Why is it a Goldmine for Attackers?
- Understanding OSINT
According to Wikipedia, Open Source Intelligence (OSINT) refers to the collection and analysis of publicly available information. This includes data from social media platforms, company websites, public databases, forums, and more. While OSINT is a valuable tool for security professionals, journalists, and researchers, it’s also a treasure trove for cybercriminals.
- Why Attackers Love OSINT
Attackers use OSINT because it’s:
– Free and easily accessible: No need for hacking skills to gather public data.
– Highly effective: Personal details make phishing attacks more convincing.
– Legal to collect: Since the information is publicly available, there’s no legal barrier to its collection.
– Usage at industrial scale: Data can be integrated into cyberattacks at industrial scale
By leveraging OSINT, attackers can create fully automated and highly targeted and credible phishing campaigns that are far more likely to succeed, even if you are an educated professional, who can easily see spelling mistakes and common phishing emails, like lost relatives abroad or a child losing his/her phone.
So, how do the bad guys benefit from it?
How Your Digital Footprint Fuels Phishing Attacks
1. Profiling Targets for Spear Phishing
Spear phishing is a highly targeted form of phishing where attackers tailor their messages to specific individuals or organizations. OSINT plays a critical role in this process.
– Web & Social Media Scraping: Attackers scour platforms like LinkedIn, Facebook, and Twitter to gather personal details such as job titles, relationships, and interests.
– Company Websites: Information about employees, organizational structure, and even email formats can be extracted from corporate sites.
– Public Records: Data from government databases, such as business registrations or property records, can provide additional context.
With this information, attackers can craft emails that appear to come from a trusted colleague, boss, or business partner, increasing the likelihood of success.
2. Creating Convincing Lures
Phishing emails often rely on urgency or curiosity to trick victims into clicking malicious links or downloading attachments. OSINT helps attackers create lures that are highly relevant to their targets.
– Current Events: Attackers monitor news and social media to exploit trending topics, such as a recent data breach or insurance review you company underwent recently.
– Industry-Specific Jargon: By researching a target’s industry, attackers can use technical terms and insider knowledge to make their emails seem legitimate.
– Personalized Content:
Details like a possible victim’s recent vacation (gathered from social media) can be used to craft believable scenarios. Attackers analyze the context of their targets – such as job roles, hobbies, or even recent life events – to create emails that feel relevant and urgent. For example, a phishing email might reference a recent conference the victim attended or a project they’re working on, making the message appear legitimate and increasing the likelihood of success.
3. Spoofing Identities and Domains
OSINT helps attackers impersonate trusted entities with alarming accuracy.
– Email Spoofing: By analyzing email patterns (e.g., firstname.lastname@company.com), attackers can create fake addresses that look genuine.
– Domain Cloning: Attackers use OSINT to identify legitimate domains and create lookalike versions (e.g., “company-security.com” instead of “company.com”).
– Fake Social Media Profiles: Attackers may create fake profiles of executives or colleagues to establish trust before launching an attack. Studies have shown that LinkedIn is one of the most abused platforms for such scams, with a 2023 report revealing that 52% of professionals have encountered fake profiles, and 1 in 5 phishing attempts originate from social media platforms like LinkedIn. These fake profiles are often used to build rapport with targets before delivering malicious links or requests.
4. Exploiting Weaknesses in Security Posture
OSINT can reveal vulnerabilities in an organization’s security practices, making it easier for attackers to bypass defenses.
– Employee Information: Publicly available data can reveal which employees have access to sensitive systems.
– Third-Party Vendors: Attackers may target less-secure vendors or partners as a backdoor into an organization.
– Password Resets: Personal details like pet names or birthdays (often shared on social media) can be used to guess security questions to hack passwords.
Real-World Examples of OSINT-Driven Phishing
Example 1: The 2024 Instagram Voting Scam
In March 2024, a Reddit user reported that their Instagram account was hacked after falling victim to a phishing scam. The attacker sent a direct message (DM) from a profile the victim thought they recognized, asking them to click a link to vote in a poll. When the victim clicked the link, they were directed to a fake Instagram login page and prompted to enter their username and password.
After entering their credentials, the hacker changed the account’s email, phone number, and enabled two-factor authentication (2FA), locking the victim out. Then, demanded payment to return the account.
Despite submitting over 30 selfie authentication videos and contacting Meta’s customer service multiple times, the victim was unable to regain access to their account.
Source: Reddit
Example 2: The CEO Fraud Scam
In a classic CEO fraud attack, cybercriminals used LinkedIn to identify a company’s CFO and their reporting structure. By analyzing publicly available information, they determined the CFO’s role, the CEO’s email format, and the company’s internal processes.
The attackers then spoofed the CEO’s email address and sent an urgent request to the CFO, instructing them to transfer $1.2 million to a fraudulent account for a “confidential acquisition.” The email appeared legitimate because it referenced real projects and used the correct corporate tone.
This scam is not isolated. According to the FBI’s Internet Crime Complaint Center (IC3), CEO fraud scams, also known as Business Email Compromise (BEC), resulted in $2.7 billion in losses in 2022 alone. The use of OSINT to gather precise details about targets has made these attacks increasingly effective.
Source: FBI’s Internet Crime Complaint Center (IC3) – 2022 Report
Example 3: The Ubiquiti Networks Breach
In 2021, attackers used OSINT to identify employees of Ubiquiti Networks, a global technology company. They sent phishing emails posing as IT support, urging employees to reset their passwords via a fake portal.
The attackers gained access to Ubiquiti’s systems and attempted to extort the company for $50 million in cryptocurrency. While the exact financial loss was not disclosed, the breach severely impacted Ubiquiti’s reputation and stock price, which dropped by 20% following the disclosure.
This incident highlights how OSINT-driven phishing can lead to not only financial losses but also long-term reputational damage.
Source: Ubiquiti Networks Breach Disclosure (2021)
From Oversharing to Overpowering: How to Beat Phishing at Its Own Game
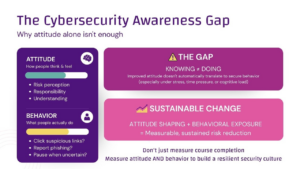
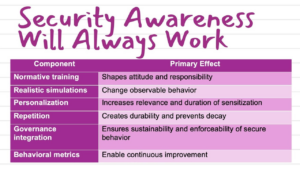
While technical defenses like firewalls, email filters, and multi-factor authentication (MFA) are essential, they’re not enough on their own. The human factor remains the weakest link in cybersecurity, and attackers know it. They exploit human error through highly sophisticated phishing campaigns, making awareness and education your most critical line of defense. Here’s how you can build a culture of cybersecurity awareness to become less vulnerable to OSINT-driven phishing:
Limit Your Digital Footprint
- Be Mindful of What You Share Online:
Avoid posting sensitive details like your work projects, or personal milestones on social media.
- Adjust Privacy Settings:
Restrict who can view your profiles and posts on platforms like LinkedIn, Facebook, and Twitter.
- Drill is Good: Launch Awareness Campaigns:
Educate employees about the risks of oversharing online. For example, our solution at CYBERDISE offers tailored training programs to help employees understand how their digital footprint can be exploited.
Promote a Culture of Vigilance
Phishing attacks succeed because they catch people off guard. Building a culture of vigilance can help employees recognize and resist these threats.
- Spot the Red Flags:
Train employees to identify common phishing tactics, such as urgent requests, unfamiliar senders, or suspicious links.
- Think Before You Click:
Encourage employees to pause and verify before clicking on links or downloading attachments, even if the email appears to come from a trusted source.
- Report Suspicious Activity:
Create an easy process for employees to report potential phishing attempts to your IT or security team.
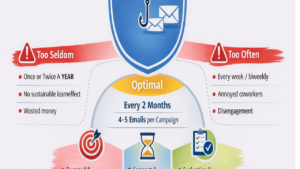
Conduct Regular Phishing Simulations
Awareness is only effective if it’s put into practice. Regular phishing simulations can help reinforce good habits and identify areas for improvement.
- Simulate Real-World Scenarios:
Use realistic phishing emails that mimic OSINT-driven tactics to test employee responses.
- Provide Immediate Feedback:
If an employee falls for a simulated phishing attempt, offer constructive feedback and additional training.
- Track Progress:
Measure improvements over time and celebrate milestones to keep employees engaged.
All of this is possible and easy to do with our latest version of CYBERDISE solution.
Foster a Collaborative Security Mindset
Cybersecurity is a team effort and definitely not a one time activity. Encourage employees to look out for one another and share their experiences.
- Create a Supportive Environment:
Make it clear that reporting mistakes or suspicious activity is encouraged, not punished.
- Reward Vigilance:
Recognize employees who successfully identify and report phishing attempts.
- Build a Community:
Use internal communication channels to share tips, updates, and success stories related to cybersecurity.
CYBERDISE Awareness: Your Partner in Building a Human Firewall
For us at CYBERDISE Awareness, it’s proven that awareness is the foundation of cybersecurity. Our tailored training programs, phishing simulations, and awareness campaigns are designed to transform your employees into a human firewall – your strongest defense against OSINT-driven phishing attacks.
Want to learn more or have questions? Contact us today and we will get back to you very quickly!