When Employees Report Suspicious Emails - It Really Matters How it Happens and What!
Published Date:
- February 4, 2026
Promoting Secure Behavior: Cyberdise V3.0 and higher offers two important new features: the email threat agent and automated incident feedback.
The Human in an AI-Driven Threat Landscape – AI did overpass the human in writing phishing emails in 2024 – already two years ago[1]. It is therefore not surprising that nowadays, virtually all phishing attacks are created by AI agents. They write more convincing phishing, in a personalized way and they can process huge volumes of messages at almost no cost. There will always be malicious messages that outsmart even the best filters and end up in your mailbox. And these will be all the more dangerous.
So, organizations must empower the employees and IT-engineers and they should respond with the same level of AI-enabled automation. That’s why Cyberdise applies AI where it matters most:
- At the moment of employee action when he starts the Phish-Button reporting process
- During incident triage
- In behavioral feedback loops
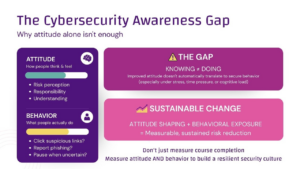
Reporting Without Clarity – It Really Matters What Happens After an Employee Report a Suspicious Mail –Most corporate cybersecurity programs instruct employees to “report suspicious emails.” When using most phishing buttons, there is no response after use, and clicking away the “thank you” message steals another half second from the user’s daily routine.
Employees are almost always left in the dark about the next steps, which undermines their personal commitment. What happens after the report is often unclear, slow, or manual.
Cyberdise addresses this weakness. These two new features available in Cyberdise V3.0
- Email Threat Agent and
- Automated Incident Feedback
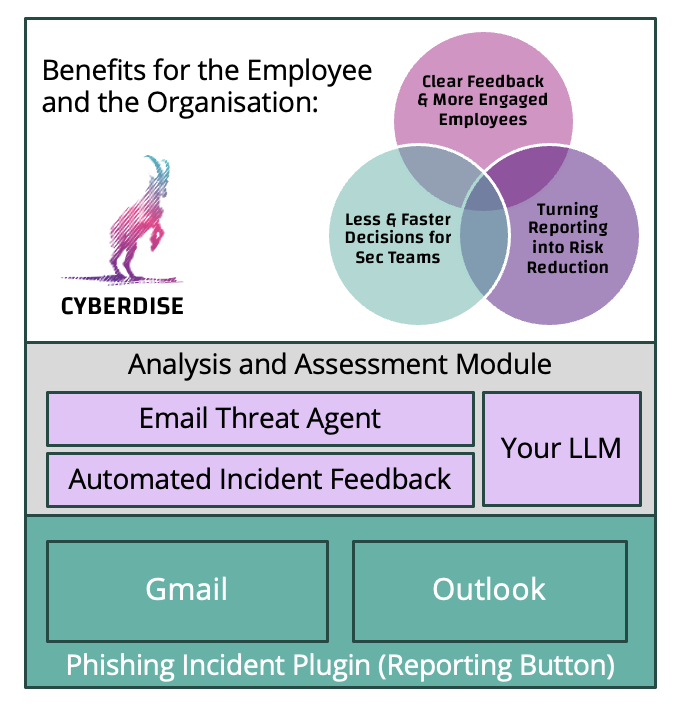
turn every reported email into a measurable security measure, not just a forwarded message. The advantages achieved are significant: Three great benefits are guaranteed:
- Clear Feedback and More Engaged Employees Without Extra Work
- Less and Faster Decisions for Security Teams
- Turning Reporting into Measurable Risk Reduction
Benefit 1: Clear Feedback and More Engaged Employees Without Extra Work
With Automated Incident Feedback in Cyberdise Awareness 3.0 using the Phishing Incident Plugin, reporting an email no longer ends in silence. After an employee reports a suspicious message, they automatically receive feedback. The answers given to the user can include the Email Risk Score and they are delivered in a consistent and configurable way, without requiring any manual response from the security team.
This matters because engagement needs a dialogue. The incident feedback mechanism maintains this dialogue and keeps users involved instead of leaving them guessing or becoming disconnected. Employees immediately see that their action had value, which intensifies trust in the threat reporting process and encourages them to stay alert.
For the organization, the impact goes beyond convenience. Employees learn while acting, not months later in a training session. Reporting feels useful rather than ignored, and good behavior is reinforced at the right moment. Over time, reporting rates may improve, false positives can be better understood, and changes in engagement and security behavior become measurable.
In this way, reporting becomes an active contribution to the organization’s security culture, not a black hole where messages seem to disappear. The answers given to the user in the behavioral feedback loop are based on customizable, standardized answers in order to avoid that there is a direct link between external LLM and the user.
Benefit 2: Less and Faster Decisions for Security Teams
Today, a reported email often ends up in a shared mailbox or a ticket system, even in organizations with a SOC. Someone still has to manually inspect the message, classify it, and decide what to do next. This slows down response times and consumes resources, especially when reporting volumes increase.
With the Email Threat Agent in Cyberdise, this process changes fundamentally. Every reported email is automatically analyzed by the agent and an Email Risk Score is calculated. It indicates how likely the email is a malicious one. This score is shown directly in the Incident Console, giving security teams immediate context without manual effort.
For the organisation, the value is clear: Security teams get a prioritization having real threats first instead of treating all reports equally. Less time is wasted on harmless emails, response times improve, and potential damage is reduced. At the same time, the process scales smoothly, even when reporting volumes rise. In simple terms, not all alerts are equal anymore.
Benefit 3: Turning Reporting into Measurable Risk Reduction
From a management viewpoint, the key question is always: “Does this actually reduce risk?”
The Email Threat Agent and Automated Incident Feedback address this directly through:
- Better prioritization
- Stronger reporting culture
- Lower operational overhead
By automatically assessing reported emails, high-risk incidents are identified and handled first, while low-risk noise no longer blocks response capacity. This allows security teams to focus their time where it has the greatest impact.
At the same time, these features strengthen the reporting culture. Employees better understand why reporting matters, and consistent feedback increases confidence and improves their reporting behavior over time.
And last but not least this happens without increasing workload, as manual triage and individual follow-ups are reduced and processes become more predictable.
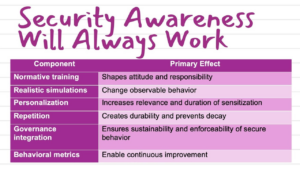
The result is not just higher awareness, but improved operational resilience.
We’re excited to share more cybersecurity insights, news, and updates with you in the upcoming editions of this newsletter. However, if you don’t find this helpful, we’re sorry to see you go. Please click the unsubscribe button below.